
Watch Dmitry’s discuss on risk-based testing challenges on the current QA Monetary Discussion board.
Introduction
There are 4 predominant challenges groups normally face whereas implementing automation testing — or any testing typically:
• Protection — means to monitor quantity of necessities being verified
• Take a look at knowledge — means to put together legitimate knowledge belongings to check with
• Configuration — means to establish and supply required testing setup and setting and ensure execution goes as designed
• Reporting — means to articulate testing outcomes for determination making
The business is in actually good condition relating to coping with these challenges. There are many nice instruments out there to assist us construct our take a look at administration system, so a typical software program pipeline is a superposition of those instruments.

However as our merchandise and processes mature, new challenges come up, corresponding to:
- Protection — is it attainable to use dynamic risk-based testing?
- Take a look at knowledge — tips on how to function shared take a look at belongings and system states?
- Configuration — tips on how to handle an ever-growing variety of distinctive execution pipelines and function them successfully?
Let’s dive in and attempt to reply these questions.
Threat-based testing
Threat is the likelihood of an unexpected occasion that may negatively have an effect on the conduct of a software program product and, due to this fact, the whole enterprise. Threat identification, evaluation, and mitigation are thus very important elements of any SDLC. These actions play key roles in product launch planning, particularly for companies providing 24/7 service, like our shoppers, who’re inventory or foreign exchange brokers and cryptocurrency exchanges.
Threat-based testing is a method that makes use of danger evaluation to pick and prioritize take a look at suites and take a look at essentially the most essential and risk-prone blocks first.
Threat-based testing is important for Agile groups working in intensive sprints, as it’s one of the simplest ways to get the very best attainable high quality inside a given timeframe. And most significantly for automation groups: risk-based testing is relevant to costly varieties of take a look at automation.
To grasp that, let’s look into the ‘costly’ half, as some might say — ‘automation is free, it prices nothing to run as soon as written’. Nicely, it prices one thing — let’s do the straightforward maths.
Combinatory overdose drawback
In a comparatively widespread buying and selling system, there are two account varieties (Money and Margin). One can use order varieties (Market, Restrict, or Cease) with 5 time in pressure 1 directions to purchase or promote belongings (shares, bonds, funds, metals, futures, choices, Foreign exchange, CFDs or Crypto). Orders are positioned in order to be triggered by worth, and you’ll edit or cancel them, whereas, relying on the present market scenario, the system can expire, reject or fill them, or fill them partially.
Due to this fact, exhaustive testing of such a easy system would require
2 × 3 × 5 × 2 × 9 × 8 = 4320 combos
Let’s assume we’ve got completely steady, predictable and bug-free UI automation giving us 30 seconds per mixture. On this case, operating these exams in 10 threads will take 3.6 hours for full execution. And that’s not even counting in different use-cases, like registration, place administration, account assertion and reporting actions, and so on. Clearly, 3.6 hours isn’t acceptable for any CI/CD course of, and produces extra CO2 than sense.
Answer
To steadiness advantages and bills, execute solely a specific subset of automated exams. Question instances by the take a look at administration system and programmatically fetch them from the codebase to create a customized execution batch.
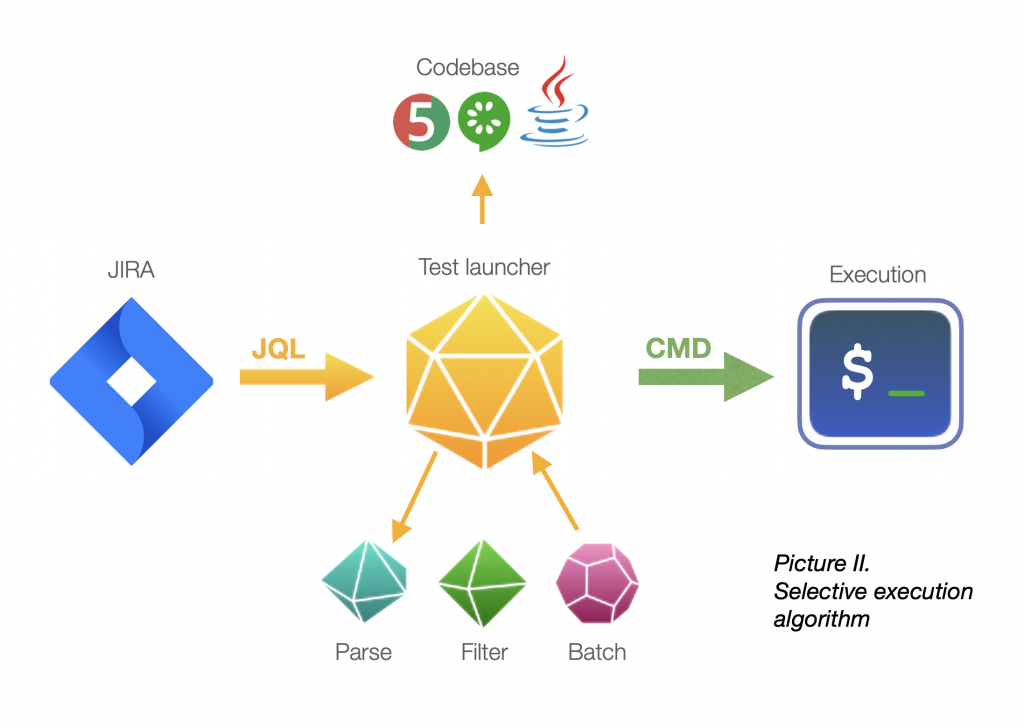
For every dash, primarily based on the product backlog, you possibly can semi-automatically tune up execution batches to cowl essentially the most essential situations.
This fashion, you not solely combine tighter alongside the risk-based supply pipeline — which is virtually nearly each industrial pipeline on the market at this time anyway — but in addition spend time debugging solely significant failures. As well as, you make the most of your computational pressure in essentially the most eco-friendly method!
Extra to learn
- JIRA API 2, XRay API3, TestRail API 4, HP ALM QC API 5
- JUnit5 launcher 6 and tags 7 NUnit TSL 8, SpecFlow Filter, Cucumber tags and run choices 9
Take a look at knowledge administration
To correctly execute take a look at, you must feed it with ready knowledge and configuration.
Static knowledge is comparatively simple to arrange. For instance, virtualized situations of a system, every provided with an in-memory database and predefined knowledge units, are fairly good for element and integration testing.
However relating to system or end-to-end testing, issues get sophisticated. Sure varieties of exams might require dynamic management over knowledge or altering the state of a operating system.
Useful resource distribution and mutability drawback
In Fintech, we’ve got a number of varieties of take a look at entities which should be, on one hand, thread-safe and lockable, and alternatively, controllable by exams. Examples embody account portfolios, buying and selling instrument configurations, or schedules.
Security. Utilizing the identical essential entity in two parallel take a look at threads normally ends in surprising conduct and cascade failures.To manage take a look at movement, you need to keep away from two parallel exams utilizing the identical entity.
Management. For a lot of buying and selling actions, the system has to alter its state or the state of an entity. The best instance is buying and selling order activation when a particular market quote ought to go by.
Answer
Make the most of the architectural sample which we name Take a look at Service sample. It’s a backend element that:
- interacts immediately with system entities;
- handles useful resource locking and distribution;
- gives easy REST API for high layer testing frameworks.
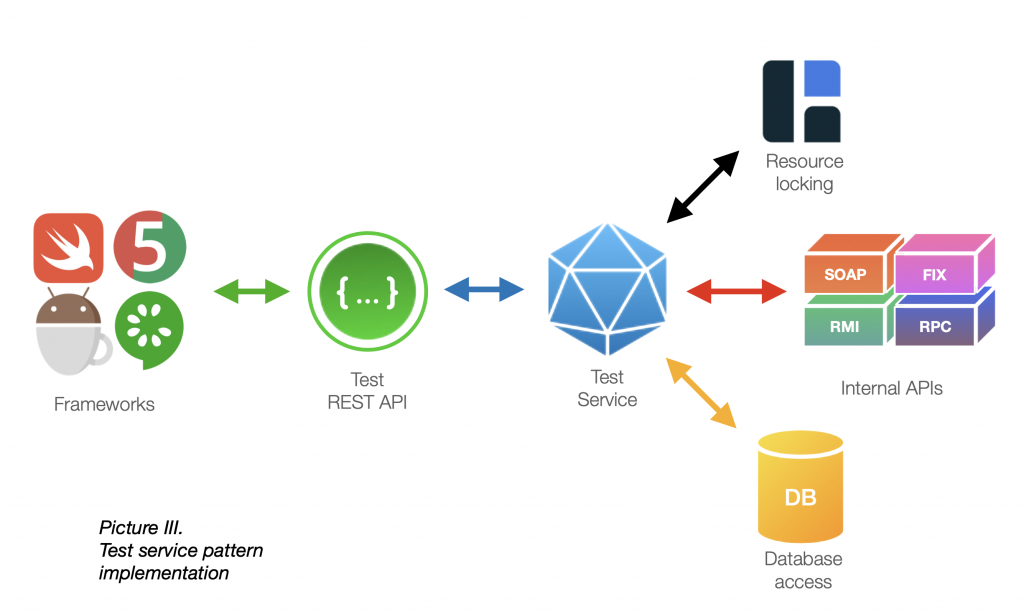
Take a look at service is constructed utilizing system APIs and normally is an integral a part of system supply. This method eases upkeep between system variations.
Take a look at service additionally handles distributed cache for useful resource locking utilizing applied sciences like Hazelcast. Each testing framework operating in opposition to a system explicitly registers its useful resource utilization, so system entities are distributed evenly and safely.
Take a look at Service REST API allows top-level frameworks to carry out considerably advanced take a look at situations and standardizes system interplay amongst all software program stacks.
The primary draw back is that Take a look at Service turns into a somewhat highly effective backdoor. It’s essential to deal with it with further care and never expose it to manufacturing.
Extra to learn
- Hazelcast documentation 10
- Distributed locks with Redis 11
- Constructing REST providers with Spring 12
Configuration
One other problem that may seem on our multi-platform, multi-targeted testing journey is the pipelines upkeep drawback. As an example it, let’s undergo an instance.
Checks are normally break up into unbiased courses referred to as purposeful areas. Each purposeful space of a product requires its personal distinctive set of preconditions and may be examined comparatively independently from different areas. Throughout automated execution, exams from the identical purposeful space are normally batched collectively first after which break up into smaller subsets if wanted.
Pipelines upkeep drawback
For buying and selling programs, examples of purposeful areas embody authentication, buying and selling actions, reporting, or third-party integrations (corresponding to liquidity suppliers, cost programs or different institutional companions). In essentially the most superior fashionable programs, the variety of FAs can go as much as 30.
If we multiply this by the typical variety of 20 patches per launch and apply riskbased technique, we get 20 × 30 = 600 distinctive execution configurations per launch.
It’s nearly inconceivable to manually keep any pipeline configuration that helps one of these course of.
Answer
This drawback may be solved by even tighter integration of present options and automation of operational routines.
It’s a good suggestion to begin with automating our construct scheduling. Test what your CI server gives as API. Chances are high you need to use it to handle your executions.
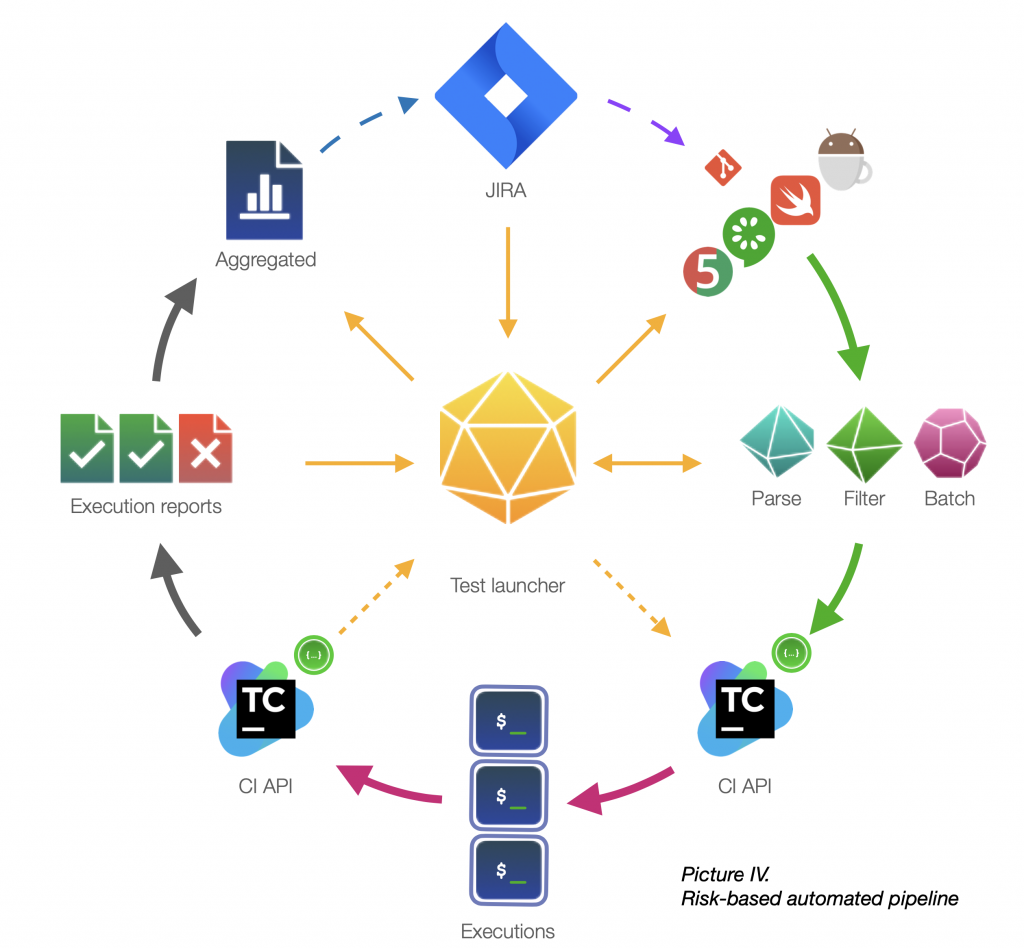
In our case, we’ve created a customized TeamCity API scheduler permitting us to separate, parameterize and execute customized execution duties in a completely computerized method.
If builds are orchestrated routinely, so shall the execution outcomes. There are just a few challenges to unravel alongside the way in which:
- Parallel builds can have considerably unpredictable execution occasions. To gather outcomes correctly, one wants to find out when all executions lastly cease. It could be required to design some listener to watch the standing of the generated executions.
- Nicely-thought logic is required on the consequence aggregation stage. If any of the take a look at situations are break up into a number of threads, verify if the aggregated consequence displays the system state.
Our answer: after splitting and producing, a take a look at launcher marks all generated builds with a singular tag. The launcher registers this tag in a standalone watcher. The watcher makes use of TeamCity API to ballot and combination the standing of all executions registered per tag. As soon as all executions underneath a sure tag have been accomplished, the watcher triggers consequence assortment. Collector will get all artifacts for a given tag, then applies hierarchical logic to compose the aggregated take a look at report.
Consequently, the general execution algorithm is virtually one-button-runs-all, whereas underneath the hood it might embody as much as 200+ generated parallel TeamCity builds.
Extra to learn
- TeamCity REST API, Jenkins Distant API 13, GitLab API 14, CircleCI API 15
- Devexperts Switchboard 16
Conclusion
With the business shifting increasingly more left and software program markets turning into increasingly more demanding, risk-based testing has already change into essentially the most generally used take a look at planning approach for a lot of Agile groups.
Whereas getting the good advantages this methodology brings, it’s vital to search out elegant options for challenges arising alongside the way in which.
Be part of us to begin discovering ones collectively.
References
- Investopedia, Time in Pressure, https://www.investopedia.com/phrases/t/timeinforce.asp[↩]
- JIRA API, https://developer.atlassian.com/cloud/jira/platform/relaxation/v3/api-group-jql/#api-rest-api-3-jql-autocompletedata-get[↩]
- XRay API, https://docs.getxray.app/show/XRAY/REST+API[↩]
- TestRail API, http://docs.gurock.com/testrail-api2/begin[↩]
- HP ALM QC API, https://admhelp.microfocus.com/alm/api_refs/REST/Content material/REST_API/Overview.htm[↩]
- JUnit5 launcher, https://junit.org/junit5/docs/present/user-guide/#running-tests-console-launcher[↩]
- JUnit5 tags, https://junit.org/junit5/docs/present/user-guide/#running-tests-tag-expressions[↩]
- NUnit TSL, https://docs.nunit.org/articles/nunit/running-tests/Take a look at-Choice-Language.html[↩]
- Cucumber run choices, https://cucumber.io/docs/cucumber/api/#choices[↩]
- Hazelcast documentation, https://circleci.com/docs/api/v2/[↩]
- Distributed locks with Redis, https://redis.io/matters/distlock[↩]
- Constructing REST providers with Spring, https://spring.io/guides/tutorials/relaxation/[↩]
- Jenkins Distant API, https://www.jenkins.io/doc/e book/utilizing/remote-access-api/[↩]
- GitLab API, https://docs.gitlab.com/ee/api/[↩]
- CircleCI API, https://circleci.com/docs/api/v2/[↩]
- Devexperts Switchboard, https://github.com/devexperts/switchboard[↩]

